In this article, we'll explore the world of JSON Web Tokens (JWT) in depth, covering everything from their fundamental concepts to their practical applications.
What is JWT?
JWT, or JSON Web Token, is an open standard that provides a secure and compact way to transmit information between different parties in the form of a JSON object. In simpler terms, it's an encrypted string in JSON format that contains sensitive information, allowing us to verify the sender's authenticity between various services.
When Should You Use JWT?
JWT is primarily used for authorization, not authentication. Authentication involves verifying the validity of a username and password, while authorization deals with validating requests to ensure they belong to an authenticated user. JWTs are ideal for scenarios where you need to authorize users, allowing them access to specific routes, services, or resources.
JWTs are also great for securely exchanging information between parties. Since JWTs can be signed using public/private key pairs, you can be confident that the senders are who they claim to be. Additionally, JWTs can ensure the content hasn't been tampered with because the signature is calculated using the header and payload.
JWT vs. Session ID
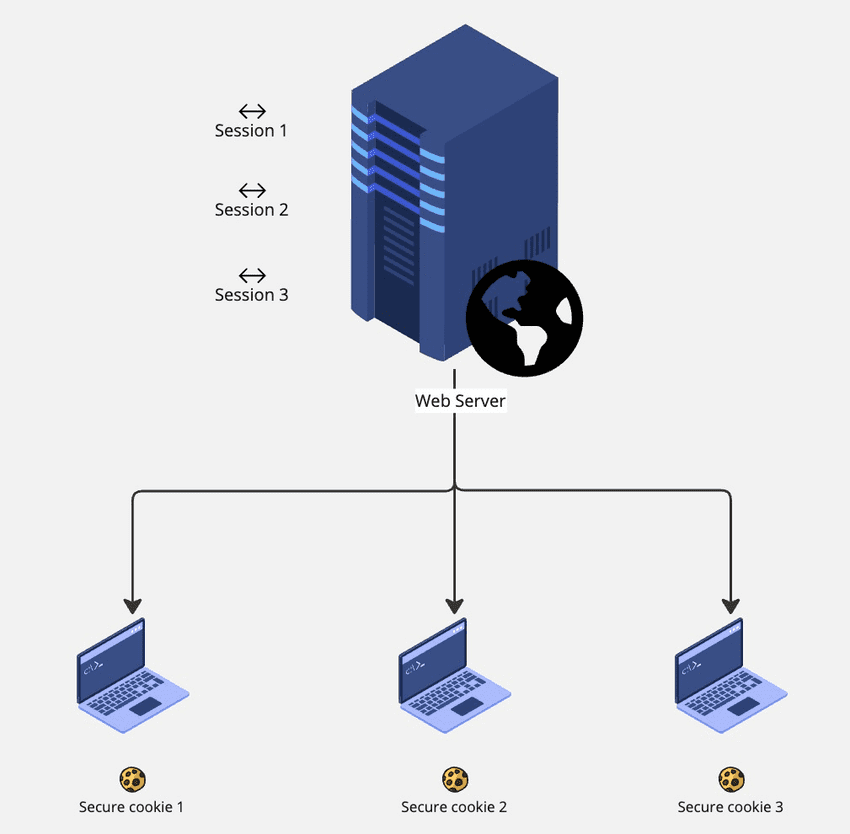
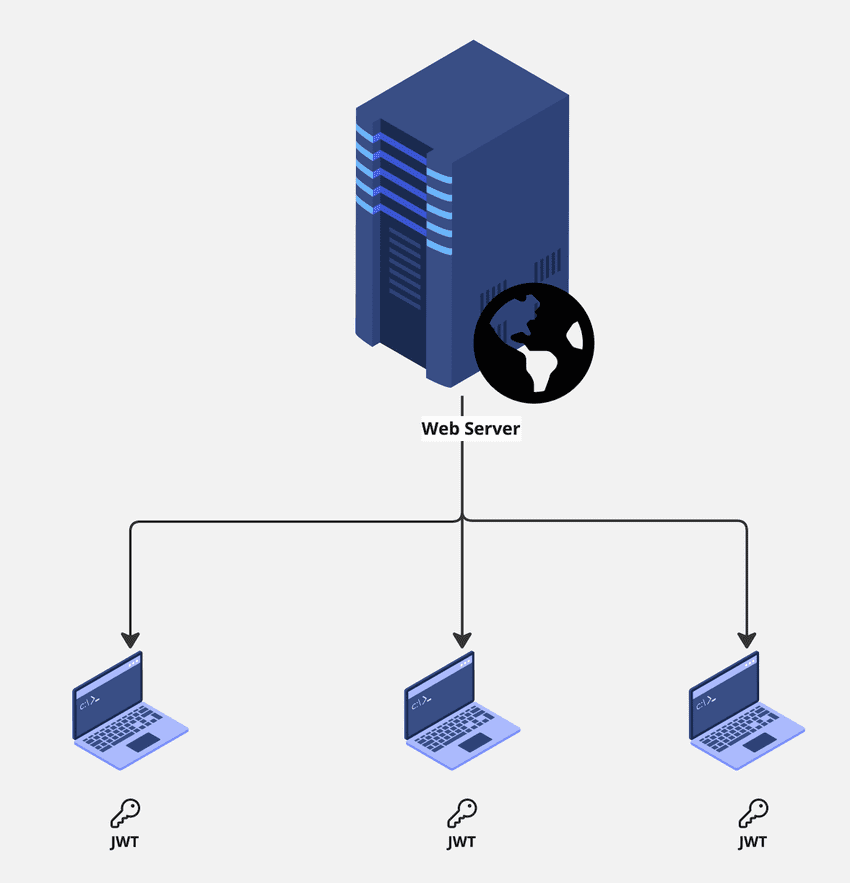
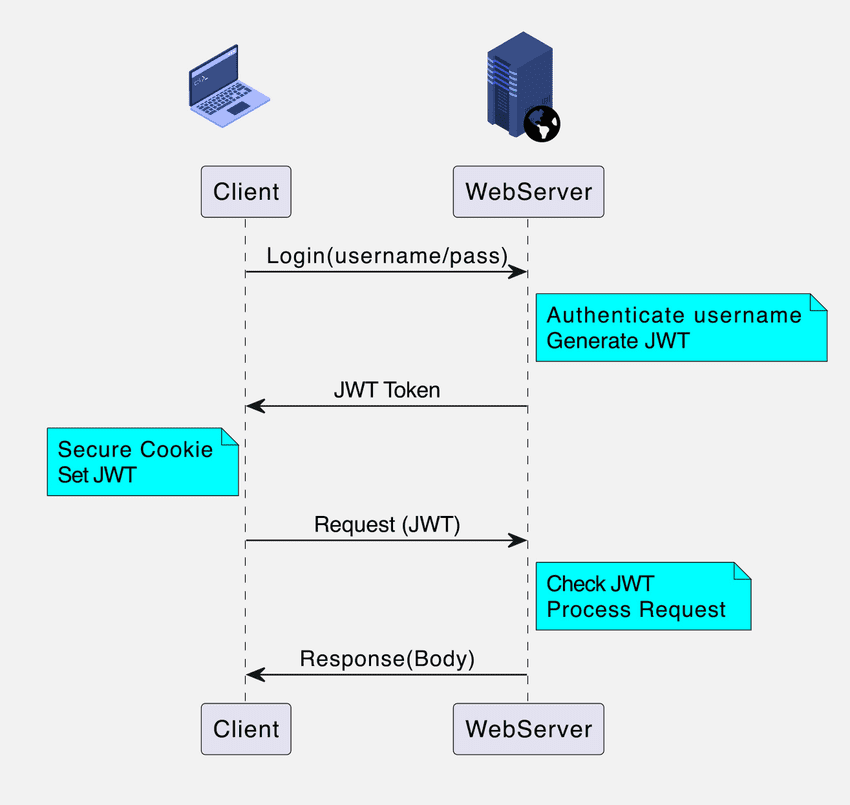
For Small Web Apps
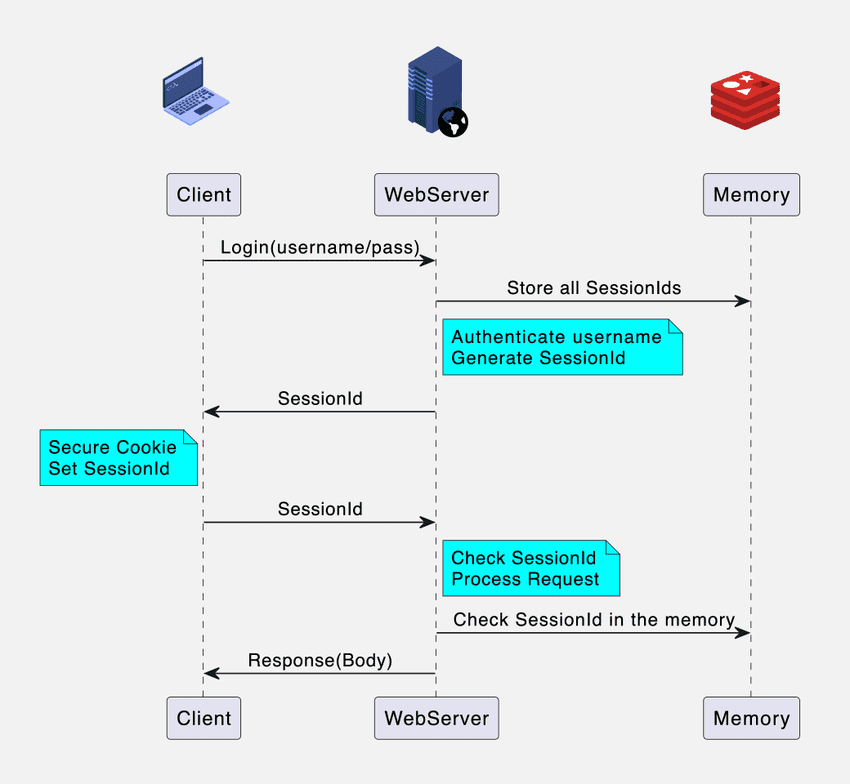
In traditional web applications, session IDs are used to authorize users. A unique session ID is assigned to each user, stored in a secure cookie on their browser and in the server's memory. The server uses this session ID with each request to verify the user's authorization.
In JWT implementation, a unique JWT is generated for each authenticated user upon login, and this token is stored in the browser's local storage or cookie. Nothing is saved on the server. With each request, the token is sent to the server, decrypted, and validated to ensure authorization. Any manipulation of the token results in rejection.
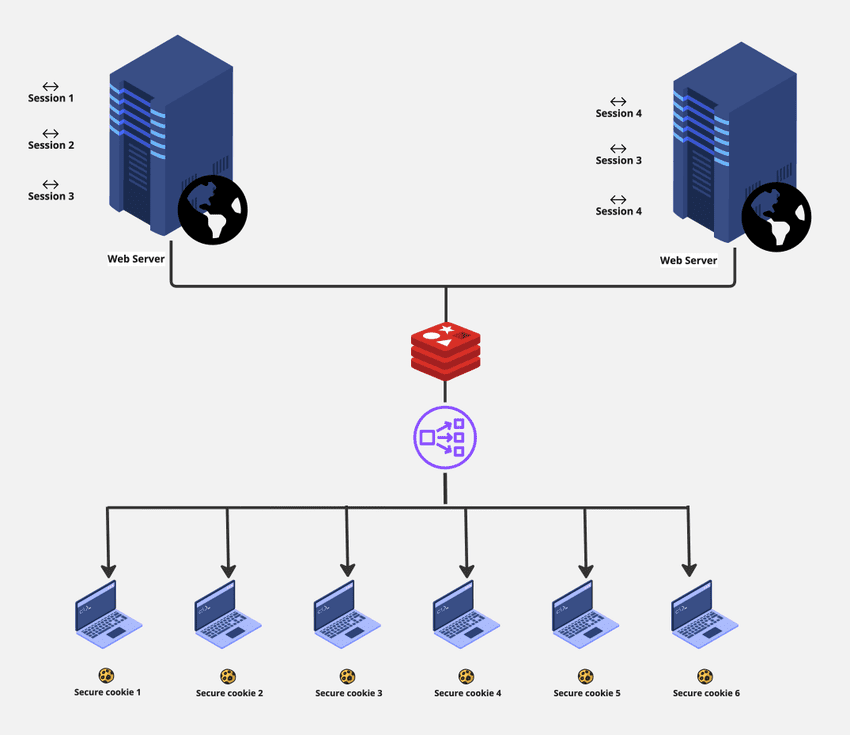
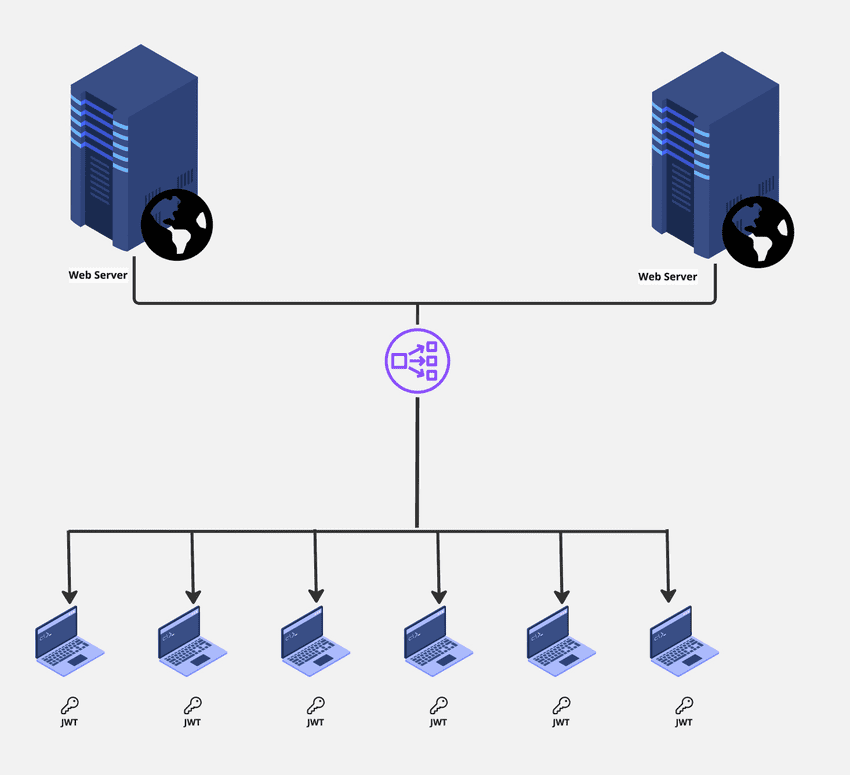
For Advanced Web Apps (Multiple Servers)
As applications grow and require scalability, traditional session ID implementations face challenges. When multiple servers are introduced behind a load balancer, ensuring session availability becomes complex. Caching is often used to address this, but it can be costly and challenging to maintain.
JWT simplifies scalability. Instead of relying on session IDs and server-side checks, JWTs contain all necessary authorization information and can be validated without server-side storage. This makes it easier to manage scalability as requests can be routed to any server without concerns about session availability. Even if one server fails, all tokens remain valid as they share the same encryption mechanism.
Quick Summary
JWT
- Nothing is saved on the server, its stored in the client inside the JWT
- Encrypted and Signed by the server
- Token contain all the user information
- All information are stored in the token itself
Session Id
- SessionId is saved on the server
- Encrypted and Signed
- SessionId is a reference to the user
- Server needs to lookup the user information and do the required checks
JWT Structure
JWTs consist of three parts separated by dots:
- Header
- Payload (Data)
- Signature
This separation visually distinguishes the token's different components. Let's delve into each part:
Header
The header typically contains two elements: the token type (JWT) and the signing algorithm (e.g., HS256 or RSA). This JSON header is then Base64Url encoded.
Payload (Data)
The payload carries claims, which are statements about the entity (usually the user) and additional data. Claims come in three types: registered, public, and private. Registered claims are predefined and recommended, while public and private claims are customizable.
Signature
The signature ensures the token's integrity. It's computed using the header and payload, encoded, and concatenated with a period. The chosen algorithm is then applied to this combination. If the resulting hash matches the third part of the token, the JWT is valid; otherwise, it's considered tampered.
Signing JWTs
JWTs can be signed using:
- A secret (HMAC algorithm)
- A public/private key pair (RSA or ECDSA)
Signed tokens verify the integrity of their claims, while encrypted tokens hide claims from other parties.
Conclusion
In conclusion, JSON Web Tokens are a powerful tool for secure information exchange and authorization in various applications. Understanding their structure and benefits can help you make informed decisions when implementing authentication and authorization mechanisms in your projects.
Learn More
- A practical guide to data collection with OpenTelemetry, Prometheus and Grafana
- Beginner's Guide to HTTP Methods and Status Codes
- Flask and SQLAlchemy: Better Data Management
Please let me know if there's anything else I can add or if there's any way to improve the post. Also, leave a comment if you have any feedback or suggestions.

Discussions